Cyber Deception Solution
Cyber Deception Solution
Fidelis Security® has been Protecting Leading Enterprises Worldwide for over 20 years
Cellphone manufacturer
Largest Defense Contractor
Convenience Store Chain
Pharmacy Chain
Mobile Service Provider
Pharmaceutical Company

Deception Technology
Deception technology in cybersecurity is a proactive approach to threat detection and mitigation. The primary purpose is to lure attackers into engaging with them, thereby revealing their presence and tactics. The key points of a deception solution include:
- Fake Assets or Deception Decoy traps
- Detection Mechanisms
- Early Warning System
- Reduction of False Positives

Fidelis Deception® - Turn Adversaries into Targets
Adversaries want your data and assets. Fidelis Deception® solution makes them believe they’ve struck gold. But what they’ve really done is trapped themselves and alerted your cyber defenders.
Our Deception Technology platform includes:
- Automatic deployment of authentic deception layers
- High-fidelity alerts eliminating false alarms
- Active sandbox analysis
- Maintained business continuity
What Sets Fidelis Deception® Technology Apart?
Fidelis Deception® shortens this time from weeks and months to just a few hours and minutes
Dramatically reduces time-to-resolution
This is achieved by quickly detecting anomalous behavior and operating inside the adversary’s decision cycle.
Fidelis Security® is #1 Proactive Cyber Defense solution in the world.
Proactive Cyber Defense
Fidelis Deception® solution gains a full understanding of your cyber terrain, including asset risk profiling, so you can anticipate attacker’s targets and proactively protect your organization.
Fidelis Security® provides you tailored solutions available on-prem as well as cloud.
On-Perm and Cloud Deception Technology
Fidelis Deception® solution works on both on-premises solution as well as a cloud solution. On cloud, the decoy software will be made available for AWS.
Threat Protection offered by Fidelis Deception®
Credential Theft
Fidelis helps you identify attackers who are searching for credentials by strategically deploying fake credentials on assets that align with their search patterns. These credentials proactively lure the attackers to access the decoy traps and applications and reveal the targeted assets.
Lateral Movement Detection
Protect your valuable data and credentials by proactively luring the attackers to access decoys, breadcrumbs and fake credentials in the Active Directory.
Deception For Active Directory
Early in the inspection phase, Fidelis Deception® identifies how the attackers are using the seeded false items in the AD. Our deception solution also secures Active Directory by looking for any evidence of the attackers' activity in the AD logs.
There’s a Reason the Most Important Data on Earth is protected by Fidelis
of the 6 US Military Branches Defended
of the 10 Largest US Government Agencies Protected
Year-to-Date High Severity Malware Threats Identified
Year-to-Date Critical Vulnerability Exploitations Attempts Detected
There’s a Reason the Most Important Data on Earth is protected by Fidelis
of the 6 US Military Branches Defended
of the 10 Largest US Government Agencies Protected
Year-to-Date High Severity Malware Threats Identified
Year-to-Date Critical Vulnerability Exploitations Attempts Detected
Fidelis Deception® Solution
Make cyber adversaries play by your rules. Fidelis Deception® reshapes your cyber terrain, giving you a distinct advantage over threats while ensuring a resilient environment.
Why is Fidelis winning against its competitors?
Our customers detect post-breach attacks over 9x faster.
Related Resources
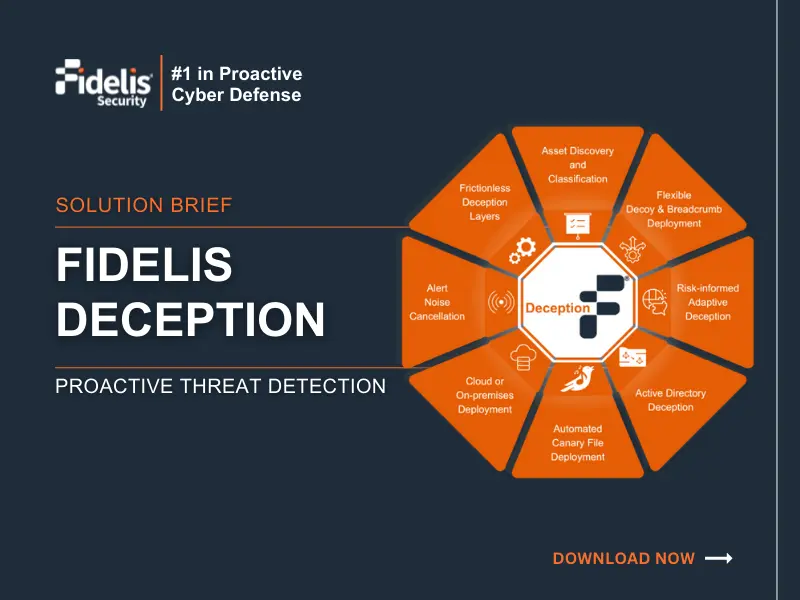
Fidelis Deception® – Turn Your Adversaries into Targets
Discover how Fidelis Deception® technologies reshape your attack surface, trap cyber adversaries, and safeguard your organization’s continuity. Download the solution

Fidelis Deception: There’s no other better trap for Attackers!
Fidelis’ deception capabilities enable you to deceive attackers and lure them into a trap, improve your ability to detect and

Fidelis Deception® fortifies Children’s Hospital with proven ROI
“Fidelis Deception® takes our network security to the next level,” the Hospital’s, IT Security Architect says.
The hospital entrusted Fidelis Security® for their network

Fidelis Deception® – Turn Your Adversaries into Targets
Discover how Fidelis Deception® technologies reshape your attack surface, trap cyber adversaries, and safeguard your organization’s continuity. Download the solution

Fidelis Deception: There’s no other better trap for Attackers!
Fidelis’ deception capabilities enable you to deceive attackers and lure them into a trap, improve your ability to detect and

Fidelis Deception® fortifies Children’s Hospital with proven ROI
“Fidelis Deception® takes our network security to the next level,” the Hospital’s, IT Security Architect says.
The hospital entrusted Fidelis Security® for their network