
#1 XDR solution for visibility of data in motion
Home » Fidelis Elevate
#1 Proactive XDR Security Platform
#1 Proactive XDR Security Platform
#1 Proactive XDR Security Platform
The only XDR platform that delivers Endpoint Security, Network Security, Deception, and Active Directory protection in one a single platform
open
extended
detection and response
No One Sees What We See
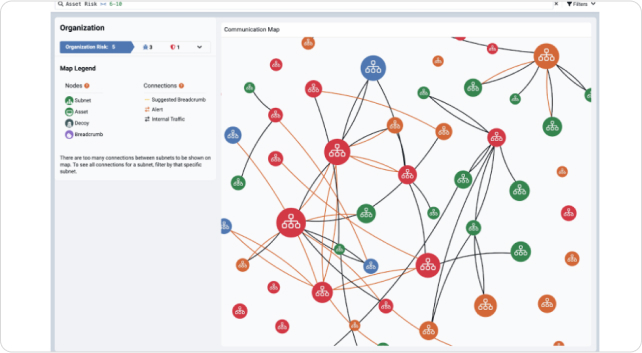
With integrated network, endpoint, and cloud visibility and analysis, our XDR platform automatically maps your cyber terrain and evaluates the risk of every asset and network path.
We operate where adversaries hide so you can catch the risks and threats that other extended detection and response tools miss.
Think Like the Adversary.
Be Ready for Anything withExtended Detection and Response
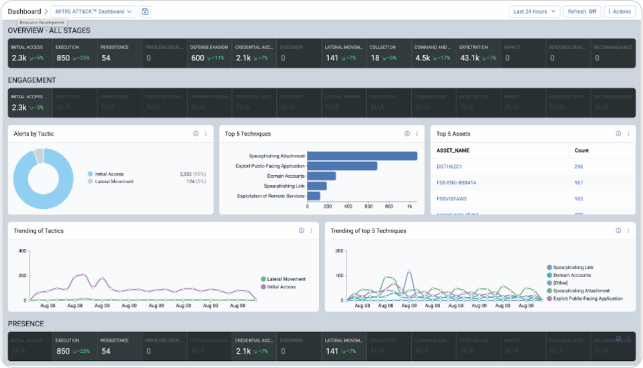
With AI-powered analysis and MITRE ATT&CK mappings, your defenders can anticipate attacker movements, respond with confidence, and remediate faster against advanced cyber threats.
Stay Resilient, Before, During and Beyond the Attack
Keep adversaries guessing and keep business operations moving.
Fidelis Security’s XDR platform uniquely integrates deception across networks and clouds, using real-time intelligence to continually build convincing decoys and breadcrumbs that lure in even the most advanced adversaries.
Fidelis Elevate® Datasheet

Why does Fidelis XDR Platform win over its competitors?
| Fidelis | ExtraHop | Vectra | Crowdstrike | |
|---|---|---|---|---|
| Comprehensive Active Directory Defense | ||||
| 300+ Field Contextual Traffic analysis | ||||
| Integrated Deception Technology | ||||
| Intelligent Active Threat Detection with MITRE ATT&CK Mapping | Limited | |||
| AI-driven Sandbox Analysis | ||||
| In-band Traffic Decryption Network DLP | ||||
| Risk-Aware Terrain Mapping |
Protect your Assets with Extended Detection & Response
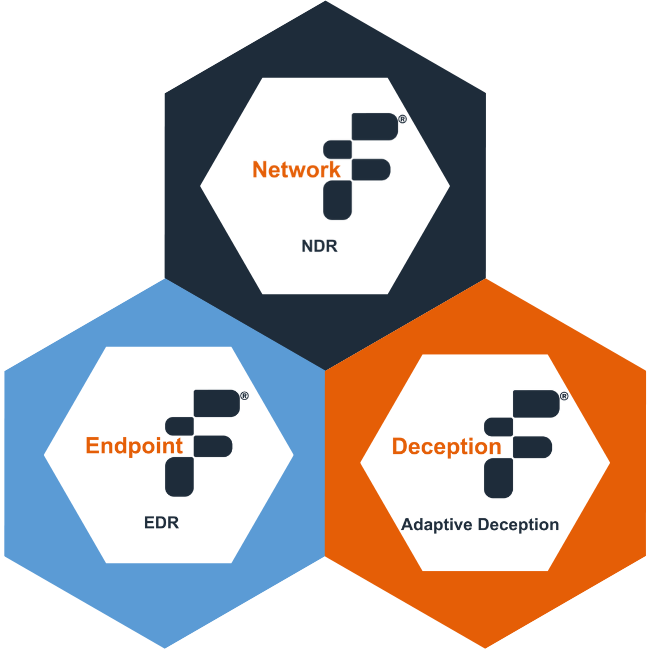
Our XDR platform has three integrated tools in one single, powerful platform that outmaneuvers adversaries with the help of:
- Deep Visibility
- Expert Forensics
- Resilient Defense
- Fidelis Network®
- Fidelis Endpoint®
- Fidelis Deception®

Better Together
- Feed intelligence between Fidelis Elevate® and Halo® to gain end-to-end protection
- Deploy risk-aware deception both on premises and in the cloud
- Understand your risks in every environment
See for yourself why we are:
Fidelis is the #1 cybersecurity solution for visibility of data in motion, with patented Deep Session Inspection™ that stops data loss
The only XDR platform with Endpoint & Network Detection and Response, Deception, and Active Directory Intercept™
Fidelis extended detection and response solution is equipped with Alert Noise Cancellation™, alerts you can trust.
