Fidelis sees
The Attack Stops Here
#1
#1
In visibility and inspection of data
in motion
50+
Industry partnerships
20+
Years of cybersecurity innovation

The Trusted Leader in Cybersecurity for Enterprise and Government
See
All your critical data, all at once
Predict
Where adversaries will strike
Respond
To cyber theaters before impact
Remain Resilient
Through and beyond a cyber attack
Trust
Your cyber alerts
Adversaries Can’t Hide from Fidelis
#1 in Proactive Cyber Defense Solutions for Enterprise and Government

Fidelis Protects the Most Critical Data on Earth
5 out of 6
7 out of the 10
Protecting the Largest Enterprises
- #1 Cellphone manufacture
- #1 Largest Defense Contractor
- #1 Pharmacy Chain
- #1 Pharmaceutical Company
- #1 Mobile Service Provider
- #1 Convenience Store Chain
The Fidelis Challenge.
No one sees what we see and we'll prove it
Run Fidelis Elevate in your enterprise environment for 30 days. We guarantee we will find threats your current provider has never even seen. If we are wrong, we will pay you $50,000 or donate $50,000 to a children’s charity of your choice.

Adversaries Hide

Fidelis Strikes

Customers Win
The Fidelis Platforms: Leading in Cybersecurity Innovation
for Enterprise Environments
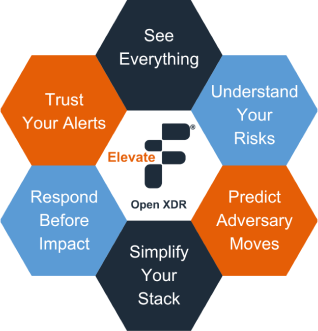
Fidelis Elevate®
The only XDR Solution that delivers Network Security, Deception, and Active Directory protection in a single platform.
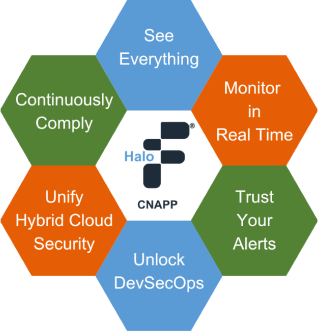
Fidelis Halo®
The only CNAPP solution for hybrid and multi-cloud environments that lowers your cloud costs.
Testimonials
What Our Client Say About Us
I know it’s unlikely to ever be 100% secure, but QGroup and Fidelis give me confidence that our security is at the highest possible level.
Fidelis achieves Gold in Cybersecurity from Merit Awards: “...a reflection of the innovations and technology advancements the industry has made over the last year.”
See for yourself why we are:
Fidelis is the #1 cybersecurity solution for visibility of data in motion, with patented Deep Session Inspection™ that stops data loss
The only XDR with NDR, Deception, and Active Directory Intercept™
Fidelis Alert Noise Cancellation™ means alerts you can trust.

Policy assignments work surprisingly well. I can just set policies for our assets and servers, and those policies apply to any new instances that we spin up.